Quantitative, Adaptive and Integrated
Cyber Quantifying Risk Service
We collecting, analyzing and interpreting data from various sources, such as cybersecurity tools, threat intelligence data and intelligence from internal and external sources.
We create a comprehensive risk reports that can be used to inform decision making and create strategies for managing cyber risk.
We develop risks mitigating strategies for your businesses, such as implementing additional security measures, investing in new technologies, or deploying a comprehensive security program.
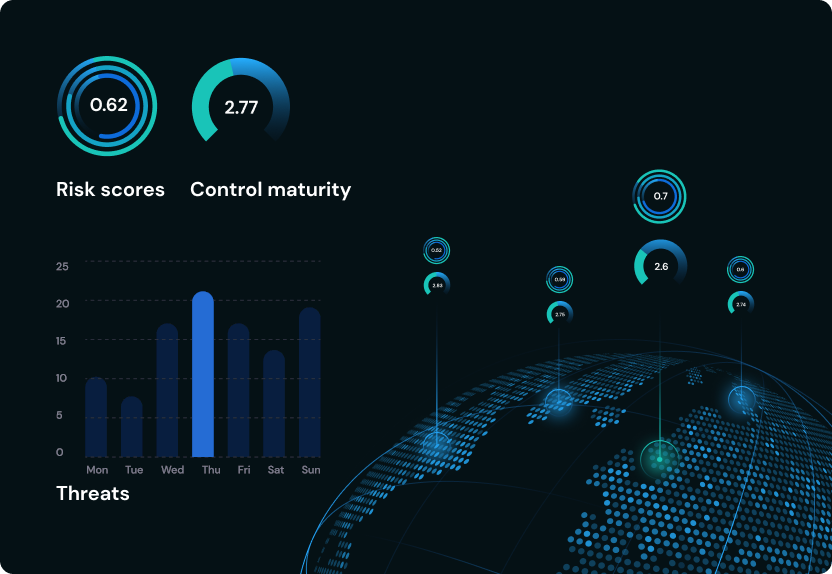
CYBER BREACH IMPACT ASSESSMENT
Analysis of the financial, legal, and reputational risks associated with a security breach. We determine the costs of a breach, the extent of the damage it might cause, and the steps that need to be taken to mitigate the risks. The assessment includes a review of the organization’s security posture, its incident response plan, its policies and procedures, and its data protection practices.
CYBER RISK ASSESSMENT
Analysis of your organization’s IT systems and networks to identify potential threats and vulnerabilities. It includes an assessment of the current security measures in place, as well as any potential risks or weaknesses that must be addressed and mitigated. The goal of a cyber risk assessment is to identify the areas where an organization’s IT infrastructure is at risk of being attacked, as well as the measures that can be taken to protect the system .
CYBER BREACH SIMULATION
We simulate attacks on your cyber system breach the security in order to identify potential weaknesses and vulnerabilities. The results of the simulations can then be used to identify and patch any security vulnerabilities that have been discovered.
CYBER PROGRAM OPTIMIZATION
We improve the efficiency and effectiveness of an existing or planed cyber security program. This includes analyzing existing processes, identifying areas of improvement and developing solutions to increase the program’s performance. It also involves identifying and implementing new technologies and strategies to improve the program’s effectiveness and reduce its overall costs.

Plan, Manage, and Respond
check measure the risks associated with cyber security threats
check identify and prioritize risks
check assess the potential financial impact of a cyber attack
check develop strategies to mitigate the risks
check informed decisions about their cyber security investments
check protect from cyber attacks and the resulting financial losses
